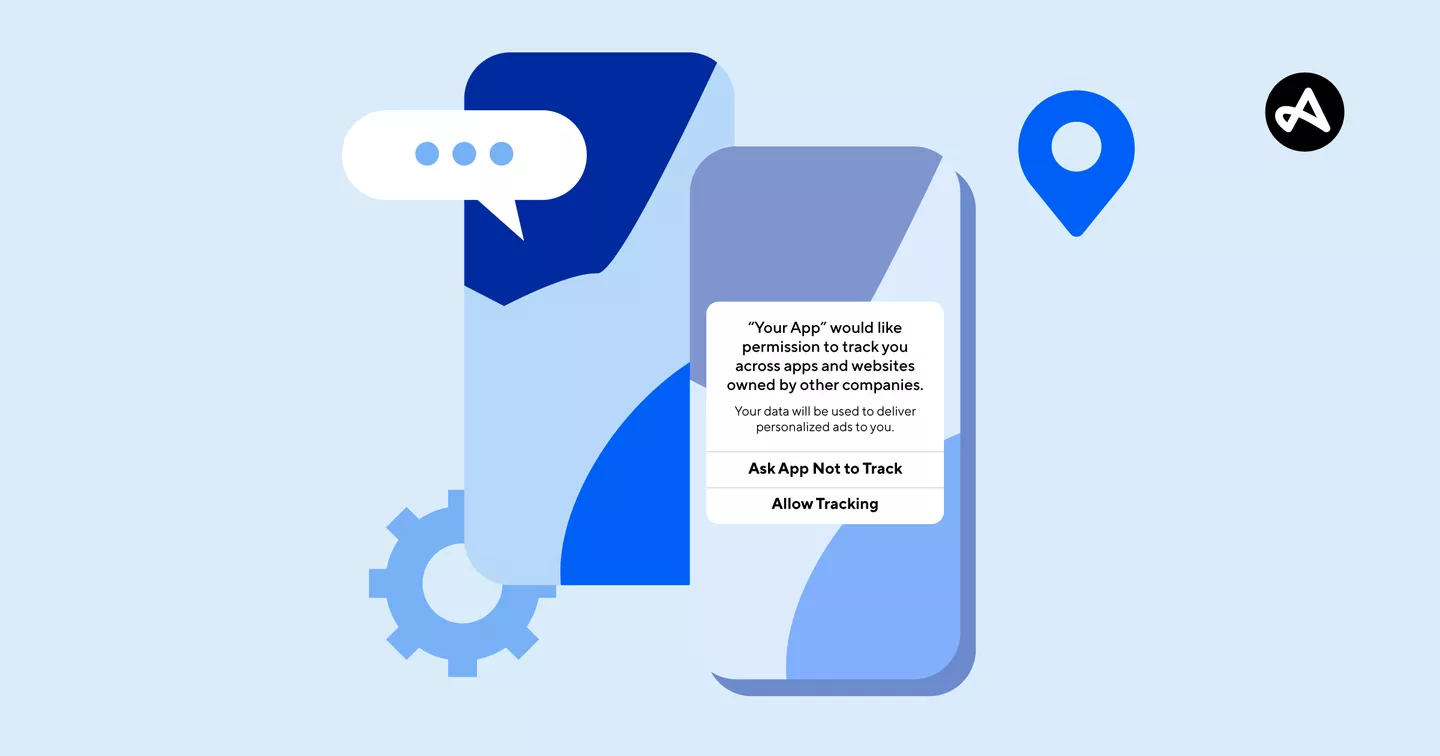
Device Permissions and Ad-trackers – what are they, and why do they matter to me?
Ah, ads. Memories of
early adopters of the internet may hear the word, and flash back to the days of
endless pop-ups no matter where we went on the net. Ads are here to stay as a part of a connected
life, but, unlike in the 90s, where it was simple “click revenue,” they’ve
taken on deeper roles; as has another special software feature:
An older concept to most computer-minded folks, but newer to
the average user, “device permissions” are specific rights that, in this case,
a user grants to a service or app, that allows it to see, do, or otherwise
manipulate something outside of the app itself.
For instance, when a free game wants access to your contacts, to share a
link, and it asks your for the ability to see your contacts list. This is a “permission.”
Back to ads for a moment: at some point in the late-90s or
early aughts, companies caught onto the fact that ads not only generate revenue
through clicks – they can be used to track who visits what, and what the user
does in their web time. Back when the
web was a simple “utility” that was used on and off, that doesn’t seem like a
bad thing at first. And on its face, it
isn’t. It allows advertisers and web
publishing companies or services to see what people like and want – so they can
tailor their material appropriately. Its
why, when you search for something like “underwear,” you find yourself suddenly
seeing underwear ads on everything from search engines to your favorite social
media services.
Enter the second decade of the 21st century. The Internet has gone from the occasional-use
utility, entertainment medium and a reference of convenience of the 90s to the
backbone of daily life. Chunky flip-phones
and brick-phones have been replaced by always-connected smartphones, and even
our appliances have become smart – everything from coffee makers to
refrigerators can be connected to the web.
Always-on set-top boxes and smart-TVs now pave the way for entertainment
as opposed to what’s on “on cable.”
Always-on internet appliances serve not only as smart, continuously
changing picture frames, calendar notifications, sports scores displays, news
blurbs and notifications letting us know where the stuff ordered from internet
marketplaces will arrive.
While this seems like the home of the 21st
century we were promised in our youths, that does come with an interesting
caveat: everything you do online, or with these devices, is being tracked.
Unlike the days of the early 90s, when we thought “okay,
that’s enough internet for today,” and turned off the family PC, the internet
is now always on, and always monitoring everything you do with it. Using the alarm clock app on your smartphone
to wake up in the morning? The fact that
the app launched at that time, is recorded by your phone. Applications that are granted permissions to
what apps you use, and when, take notice of this. Enjoy a certain form of media via email? Your phone takes notice of this – as does
other apps that have been granted permissions to see this. Insodoing, the apps will share that data with
their owners, who often use this to build a psychological profile of their
average users, so they can tailor services to them that they would like. Permissions and Ad-Tracking, when combined,
can be a powerful tool for ecommerce and while that doesn’t seem like a bad
thing on its face, what could be inferred from this if it decided to be taken
to the dark side?
Bad actors, using a “free app” as a Trojan horse can require
users to allow all manner of permissions be granted to it, in exchange for its
use. Specifically, but not limited to:
the personal information in your contact
profile, access to your contacts, your pictures and videos, your email,
etc. By taking this information from
you, with your own permission – not only can a bad actor begin to form a
psychological profile of you (i.e., your behaviors, and how you operate), but
can get very specific, detailed information on you.
For example, granting permissions to an app for access to
your email could theoretically give it unlimited access to it. So, not only can it see who you email when,
but it can also see who you get email from.
On its face, this may also seem relatively harmless. But, consider the fact that your financial
institutions may communicate with you via email. Now, the bad actor not only potentially has
your name and phone number, but also now knows where you bank.
Further, say you often communicate via email with your
parents. They may be somewhat web savvy,
but didn’t stay entirely with the times, preferring the simplicity of email, as
opposed to the “Always on” of text messaging or social media inboxing. Now, the bad actor is able to figure out the names
of your parents, if they so decided. The
names of your parents are often a question used by your financial institution
to verify you, if you were to call in via phone.
You may have taken a photo of your identification card to
keep handy in an emergency; or for some other purpose. The app, having been granted access to your
photos and videos, could potentially share this with the app’s developer, the
bad actor, or some other person or organization that has access to it. This
picture, which includes your ID number, is another question a financial
institution may use to verify you if you were to call in.
While this is an extreme example, this isn’t as farfetched
as it may seem.
In 2015, a data breach took place with the United States
Office of Personnel Management.
Targeting the Standard Form 86 (also known as “the SF-86”), this form is
the standard questionnaire used by the United States government to collect
information needed to conduct background checks, investigations and evaluations
of people who hold, or could hold positions involving national security,
requiring security clearances. This
document has to be completed in order to receive a security clearance, which
includes information on what education a prospective clearance holder has,
employment for at least ten years, any connections or ties to foreign
governments and foreign nationals, past residences, any travel abroad, among
other things.
The attack was believed to be taken by a spy agency in the
People’s Republic of China, specifically, hackers acting on behalf of the
Ministry of State Security. Information
that was obtained in the breach by the bad actor (also known as “exfiltration”)
included was the above information given in the SF-86, but also information such
as social security numbers, birth date and places, information including family
members, college roommates, personal psychological information and foreign
contacts, of current or prospective government employees – including personnel
serving in the United States Armed Forces.
Over 22 million records were affected by the breaches
(specifically, two were noted, called “X1” and “X2” by the Department of
Homeland Security. Included in the
exfiltration, were over 5 million sets of fingerprints. To date, the People’s Republic of China has
denied responsibility for the attack.
Why does all this matter, and how does it relate to your
apps?
Consider that the United States government is often viewed
as the figurative “Fort Knox” of physical and data security. Indeed, Fort Knox is a facility of the United
States government itself! If the United States government can be the
target of data exfiltration, for the apparent specific purpose of targeting
personally identifiable information and even biometrics – how can an individual
expect to protect themselves?
Unfortunately, there is no such thing as “hack proof”
electronics or data. But, when it comes
to ad trackers, and other data designed to extract your information,
particularly if its an app, service or device you specifically don’t want that
to happen, there are some proactive steps you can take to minimize your risk,
and limit any damage to your digital ecosystem:
- Utilize a separate
email for your devices, as opposed to your primary email, where you may get
banking and personal information in.
That is to say, have your phone, tablet, or other “internet of things”
devices set up on a separate email address, that doesn’t get anything vital to
your personal information security, such as your banking or other personally
identifiable information.
- Consider
permissions carefully before you grant them. Your new favorite “free” game is wanting
access to your camera, pictures and/or microphone. Consider this carefully. Does it really need these in order for you to enjoy your game?
- Consider using a
VPN service for your computers, laptops, and connected devices. Services such as Proton who I have extensive
experience with, help jacket your data connection, screens out ads and
ad-trackers, tracking pixels and other tracking
methods to keep your internet footprint far more private.
- Utilize a separate
subnet for your “internet of things” connected devices, such as your smart TVs,
smart appliances, etc. This is for
more advanced users, but, its also very effective. Basically, anything that isn’t a computer,
laptop, server or smartphone, should go here.
These help isolate your smart devices from being able to see, and
potentially exfiltrate any data, on say, your computer, laptop, media servers,
etc, from your primary computer network.
Most “internet of things” devices just need to be able to talk to the
internet – they often don’t need to specifically interact with your main
computers, servers, etc. There are
exceptions to every rule, but for the most part, they just need to see “the
cloud,” not the other devices you own.
An explanation of how this works in general, and the benefits it can
offer you, can be found here.
- Consider if you “need”
specific smart devices in your home. Sure,
we all love the convenience smart devices and the “internet of things” offers
us. However, ask yourself if it’s
needed. By keeping your digital
ecosystem free of unneeded devices, this helps tighten your home and digital
security – and eliminates a vector where ad-tracking can’t target you. For instance, if your smart coffee pot knows
you like a specific type of coffee, this can be incorporated into ad-tracking,
and steer you toward more expensive options, costing you money. Personally (just my opinion here), I can do without a smart fridge, and a
smart coffee pot.
To sum up, device permissions and ad-tracking is
more pervasive and offers more intrusion than most people tend to realize –
particularly by those who are bad actors.
In the best of circumstances, its used to provide you things of your
interest. At worst, it could be used to
compromise your digital safety and digital ecosystem, particularly in the
“always-on” connected lifestyle we now experience, that wasn’t there just a
couple decades ago.









